8 min read
6 Ways Your Centralized Identity Management Solution is Holding You Back
June 13, 2023

Identity is at the heart of every digital interaction and transaction we make, and it is the first line of defense against online fraud. And yet, most organizations are still using methods of authentication based on centralized models, which are a root cause of identity-based threats, the leading cause of cyber risk today.
Fortunately, decentralized identity solutions are gaining popularity and becoming the next step in identity management with enhanced privacy, security, and user empowerment.
In this blog post, we’ll delve into the pain points your organization may face with your current identity solution and understand why it's time to consider a different approach.
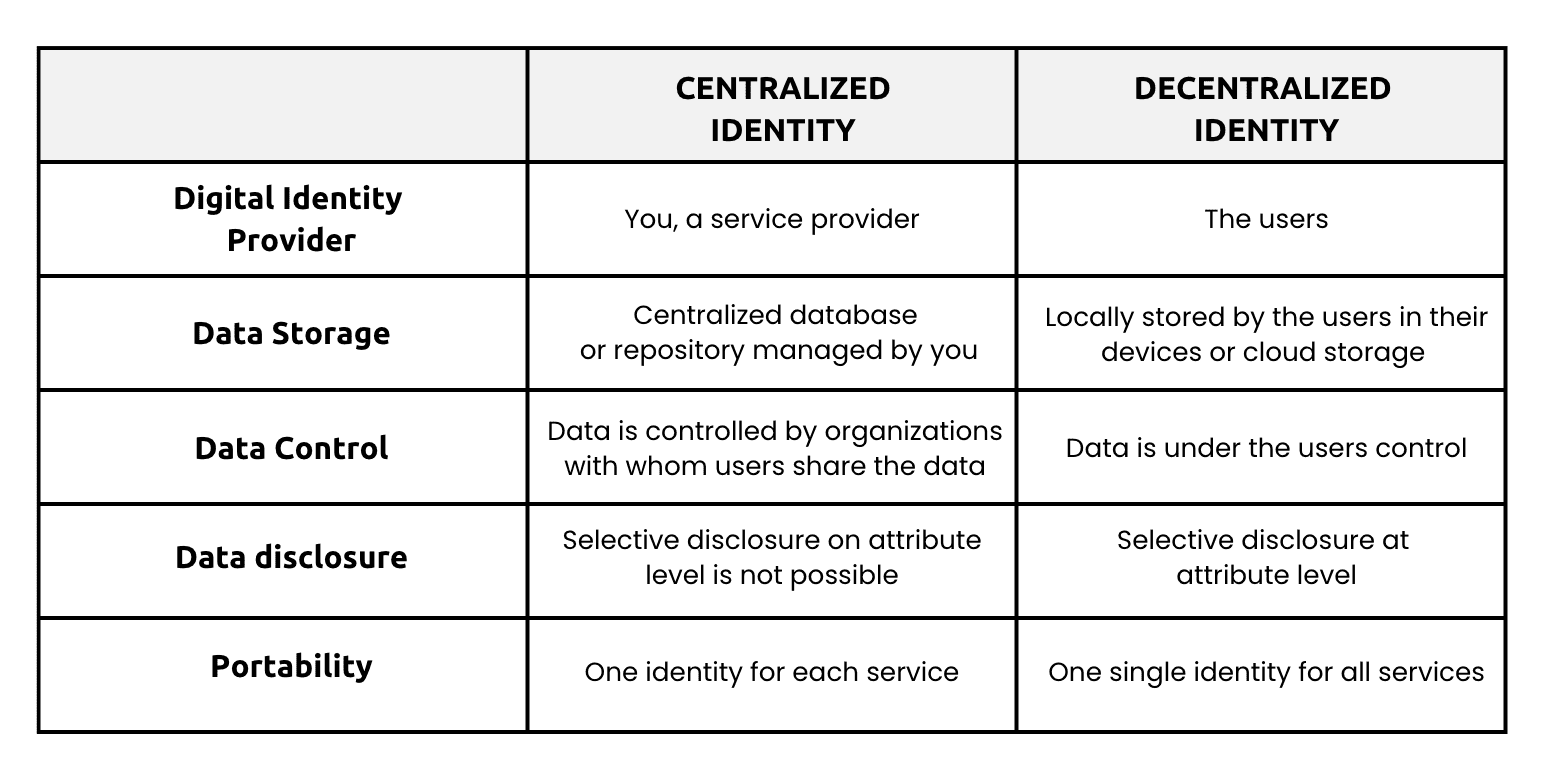
Centralized vs. decentralized identity management
But first, what is the difference between centralized and decentralized identity management solutions? The answer lies in how the data is stored and shared with others.
- In a centralized identity management system, data is stored and managed by a central authority or service provider who typically maintains a central repository or database where user identity information is stored. This includes, for example, your full name, date of birth, address, email, or financial information.
- In contrast, in decentralized identity management systems, data is stored locally by the user in the form of verifiable credentials in his device or cloud storage under their control, giving the individual ownership and control over their identity information without relying on third-party intermediaries. Sounds good, right? Please keep reading to learn more about it.
Limitations of Centralized Identity Management Solutions
1. Customer churn during onboarding
In the current fast-paced digital landscape, your users want their digital experience to be fast and simple. But here's the problem: onboarding processes can be complicated and time-consuming when relying on centralized systems for identity verification.
If your onboarding process has never-ending forms with multiple steps or requires the scanning of ID documents, or even worse, holding a paper with a handwritten date and name, you are definitely impacting your conversion rate and putting your organization at a competitive disadvantage.
While these steps and multiple layers of authentication are necessary for security reasons or compliance requirements, they can inconvenience your users, leading to fatigue and higher abandonment rates.
A 2022 report from Signicat found that financial institutions lose more than €5 billion euro to onboarding abandonment steaming from long application processes and requirements for more personal information.
The good news is decentralized identity solutions offer a way out of this frustrating cycle by providing customers with a hassle-free experience.
2. Financial losses in fraudulent transactions
One of the key issues with centralized systems is their vulnerability to forged credentials or stolen identities, as centralized identities are typically protected using recycled passwords and insufficient security.
According to the Javelin Strategy & Research Identity Fraud Study, Identity Theft Affected 40 Million U.S. Adults in 2022 Totaling $43 Billion in Losses.
Unauthorized access can result in financial losses for your organization. This can include direct financial theft, fraudulent transactions, or other illicit activities using compromised identities.
Additionally, there may be costs associated with remediation efforts, such as conducting investigations, implementing security measures, notifying affected individuals, and potential legal fees.
Besides the economic repercussions, unauthorized access can lead to a data breach, where sensitive and confidential information may be compromised, with legal and reputational consequences for your organization. We'll tackle that latest point in just a moment.
3. Brand reputation damage through data breaches
Centralized solutions are more susceptible to cyberattacks, and once malicious actors break through your defenses, it's game over. Hackers can snatch a treasure trove of personal data, including names, addresses, social security numbers, financial details, and other sensitive information.
Now, here's where things get messy for organizations. When customer data gets compromised in a data breach, the first casualty is customer trust as they start doubting your organization's ability to keep their personal information safe and secure.
But the damage doesn't stop there. The ripple effect of a data breach can send shockwaves through the brand’s reputation. Data breach news spread like wildfire, making rebuilding that trust and winning over new customers a Herculean task.
4. Data management burden
Let's talk about the data management headache that comes with centralized identity solutions. In these systems, sensitive user information and credentials are stored in a single location or database, becoming a sweet spot for cybercriminals. Organizations are, therefore, responsible for safeguarding and keeping vast amounts of user data under lock and key.
This involves implementing robust data storage systems and investing in strict security measures such as encryption, access controls, firewalls, and intrusion detection. These obligations are not only complex but also come with significant costs.
Why all the fuss? Well, failure to meet these requirements can result in data breaches, legal consequences, and reputational damage. Talk about pressure!
In contrast, decentralized identity management alleviates the data management burden in organizations by giving individuals control over their data and minimizing the need for long-term storage of sensitive information.
5. Costs associated with manual identity verification
Not long ago, in-person identity verification was the norm for regulated industries or sensitive processes like banking or vehicle ownership transfer, involving meticulous document examination, questioning, and record cross-checking. But times have changed, and despite now enabling digital onboarding processes via the provisioning of scanned identity documents, many organizations still rely on manual verification of these digital scans.
On the other side, users are burdened with repeatedly providing the same information for each different service, and organizations with validating it from scratch, resulting in wasted hours of valuable business time and resources.
Moreover, individuals are at the mercy of your organization's processes and timelines for updating their information, leading to delays, frustration, and potential errors in their profiles or records. Needless to say, not exactly the smoothest ride.
Some organizations are unaware of the true costs of manual verifications. You can achieve significant cost savings and operational improvements by adopting decentralized identity verification.
6. Struggles to comply with data protection regulations
Organizations relying on centralized identity management solutions often spend considerable time and money trying to comply with data protection regulations and Know Your Customer (KYC) obligations.
Centralized systems can present compliance challenges due to data concentration, lack of granular control, difficulties addressing data subject rights, and high compliance costs due to significant investments in infrastructure, security measures, and specialized personnel.
Failure to meet these regulatory obligations can result in hefty fines, legal disputes, and ongoing regulatory scrutiny.
On May 22, Meta was fined a record 1.2 billion euros and ordered to stop transferring data collected from Facebook users in Europe to the United States, in a major ruling against the social media company for violating European Union data protection rules.
In decentralized identity management, organizations benefit from users holding pre-verified identity information and having control over data sharing and access revocation. This shift in data control translates into easier and automated compliance with data privacy regulations and inexpensive verification processes thanks to the concept of reusable KYC.
Introducing decentralized identity management technology
Decentralized identity management, or self-sovereign identity, refers to an authentication architecture where individuals have full control and ownership over their digital identity without relying on intermediaries. In simple terms, it allows people to decide who can access their data and how it is used.
It typically leverages decentralized technologies (although not necessarily), advanced cryptography, and user-centricity via digital ID wallets to provide secure and privacy-preserving access to digital services.
How does it work and overcomes the aforementioned challenges?
New and secure cryptographic capabilities and the preference for mobile devices have opened new ways to improve the customer experience while adhering to legislation and consumer expectations around data protection - precisely what organizations are asking for.
With decentralized identity management, the onboarding process for a new customer is simple and quick. They navigate to your website, scan the QR code you’ve created for authentication with their ID Wallet, consent to share the verifiable credentials requested, and they're instantly in!
All of this happens within seconds, reducing the friction and hassle associated with creating new accounts for each service and reducing churn during onboarding processes.
These verifiable credentials are digital files issued by trusted authorities that contain information about a person, organization, or thing and that can be automatically verified by others, thus eliminating the need for manual or repeated identity verification.
They are protected with biometric and advanced encryption techniques to ensure they are tamper-proof (significantly reducing fraud) and stored by users (minimizing the need for long-term storage of sensitive information, the risk of data breaches, and costly security infrastructure).
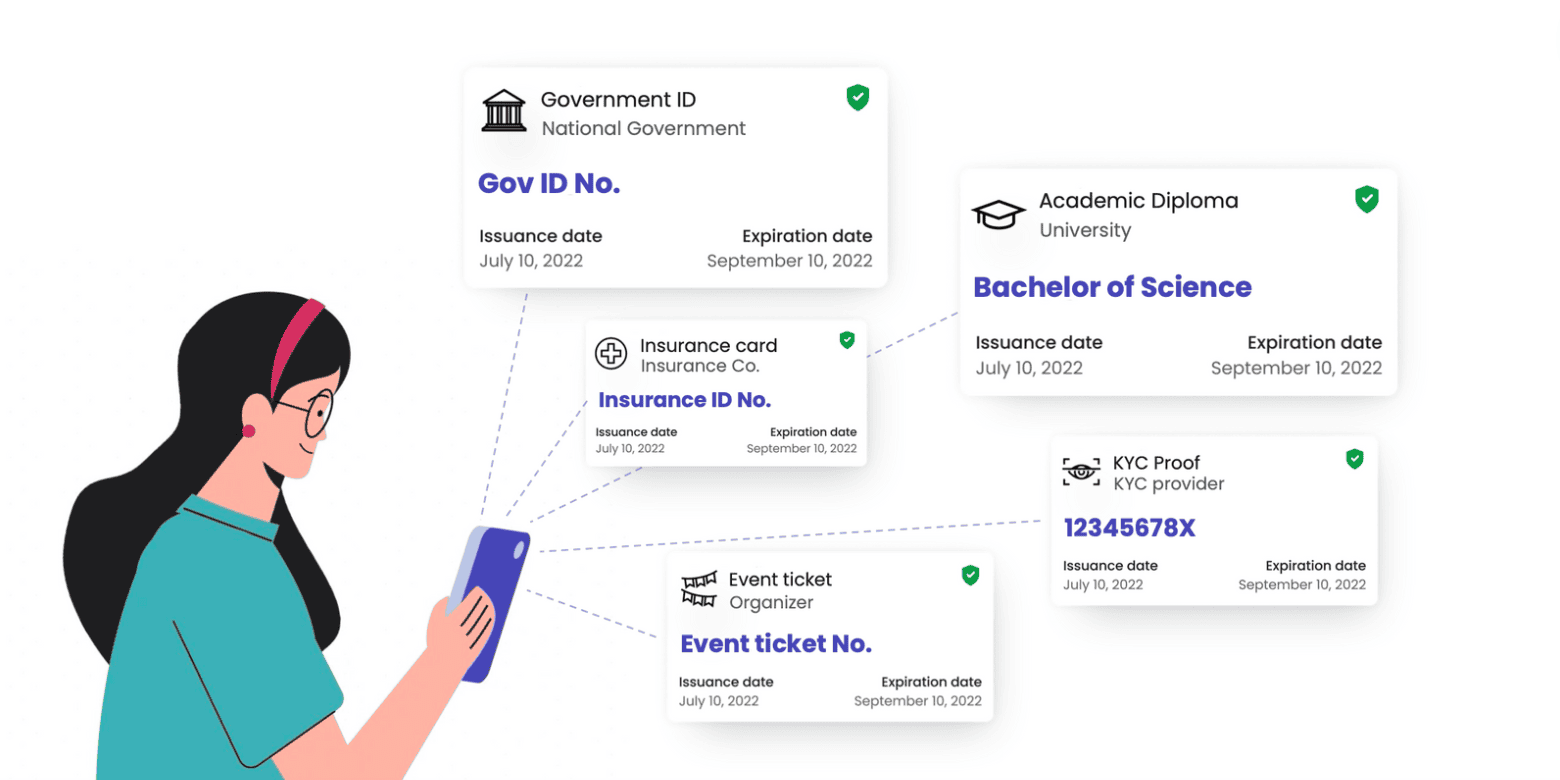
Finally, users decide with whom to share these verifiable credentials and when to revoke access, naturally complying with privacy and data protection regulations and building stronger relationships with users and authorities.
Embracing decentralized identity management solutions marks a transformative shift towards a more empowered, secure, and user-centric digital landscape.
By breaking free from the limitations of centralized systems, organizations have the opportunity to unlock seamless onboarding experiences, eradicate fraudulent transactions and shield brands from the devastating aftermath of data breaches, ensuring both organizations and users can transact with confidence and peace of mind.
At Gataca, we provide organizations with decentralized identity technology with our SaaS platform and ID Wallet. Want to learn more? Contact us for a demo, or test it out yourself for free.

Esther Saurí
Digital Marketing Specialist