12 min read
What Are Verifiable Credentials?
September 19, 2023

In this article, we dive deep into the nitty gritty of Verifiable Credentials. From what VCs are, real-world applications, and the multiple benefits they offer to their underlying components and technicalities, get ready to explore this fundamental concept of the digital identity revolution.
What are Verifiable Credentials?
Verifiable credentials (or VCs) are a standard format for the digital representation of credentials that are cryptographically secure, verifiable through machines, and that guarantee privacy by enabling methods such as selective disclosure.
In simpler terms, Verifiable Credentials are secure digital documents containing information about a person or entity that can be easily shared and automatically verified.
Verifiable Credentials are one of the pillars of Self-Sovereign Identity (SSI), a nascent technology that solves the flaws of the current identity management paradigm by allowing users to control their data and hold pre-verified identity documents in a digital wallet. Accompanying VCs in this framework are decentralized technologies (although not imperative) and decentralized identifiers (DIDs).
It's important to note that the term "Verifiable Credentials" adheres explicitly to the W3C Verifiable Credentials Data Model. This foundational specification establishes a universal format for encoding verifiable claims and cryptographic proofs within VCs.
However, digital credentials can also conform to other data models, such as ISO/IEC 18013-5, commonly known as the Mobile Driving License (mDL).
Examples of Verifiable Credentials
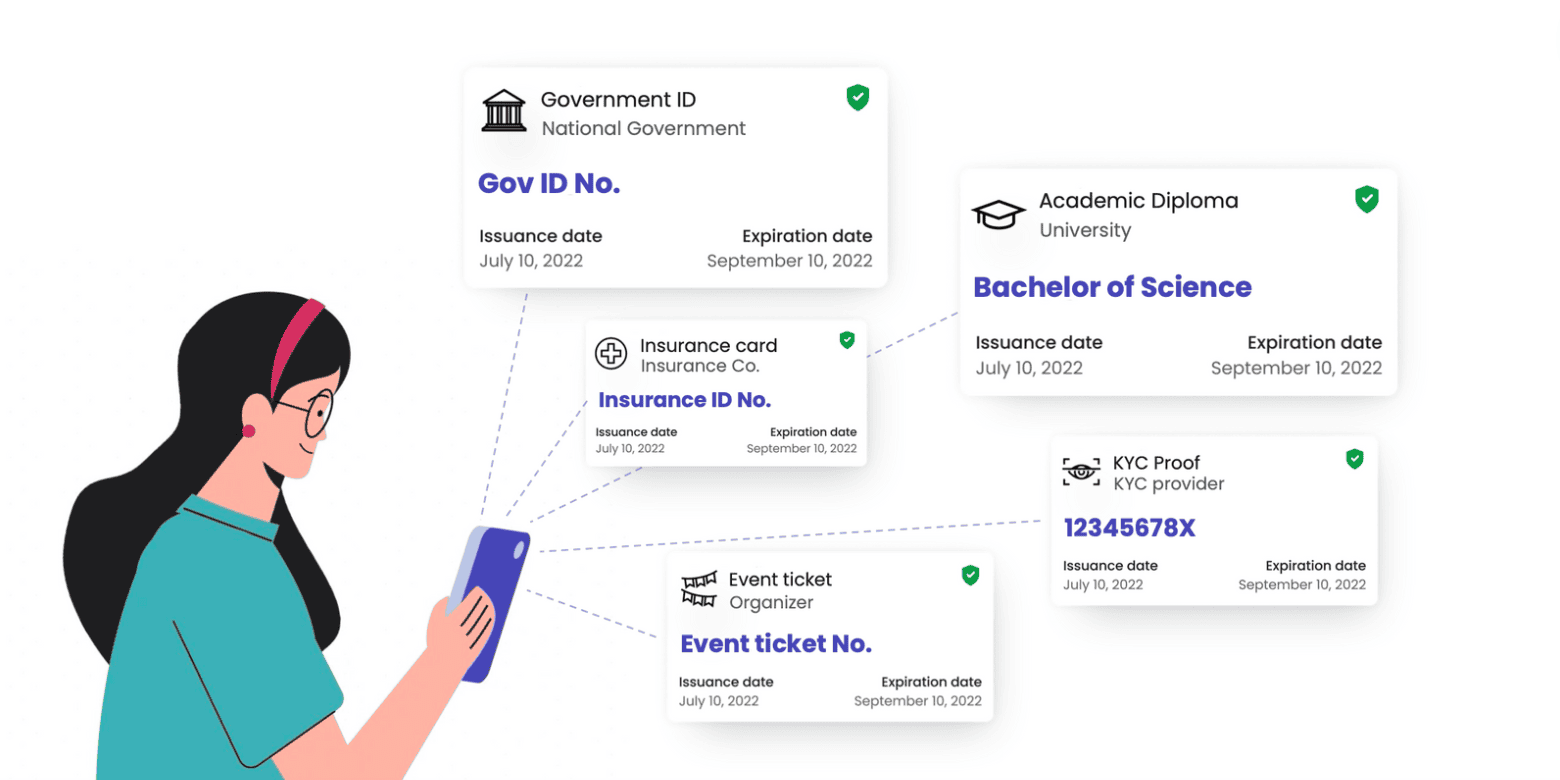
Any identity credentials, certificates, tickets, badges, and other personal documents you can think of can all take the form of Verifiable Credentials. Here are some of the most common types:
- Identity Documents: VCs can include digital versions of government-issued identity documents, such as national ID cards, driver's licenses, passports, or any other official identification document you rely on.
- Academic Certifications: Educational institutions can issue VCs for academic achievements, like diplomas, degrees, certificates, or transcripts.
- Health Records: Verifiable health records, vaccination certificates, or medical test results enable the secure and private sharing of health information.
- Membership Cards: VCs can be used for loyalty programs, club memberships, or employment ID cards providing proof of membership to a particular service or community.
- Self-Attested Credentials: Sometimes, you might need to verify identity credentials like email addresses or phone numbers. VCs can be self-attested credentials in these cases.
How Verifiable Credentials Work
To understand how Verifiable Credentials operate within the Self-Sovereign Identity (SSI) ecosystem, it is imperative to introduce the concept of Verifiable Presentation (VP).
Think of a VP as a digital envelope containing a pack of claims extracted from one or more Verifiable Credentials to present to the service provider or verifier.
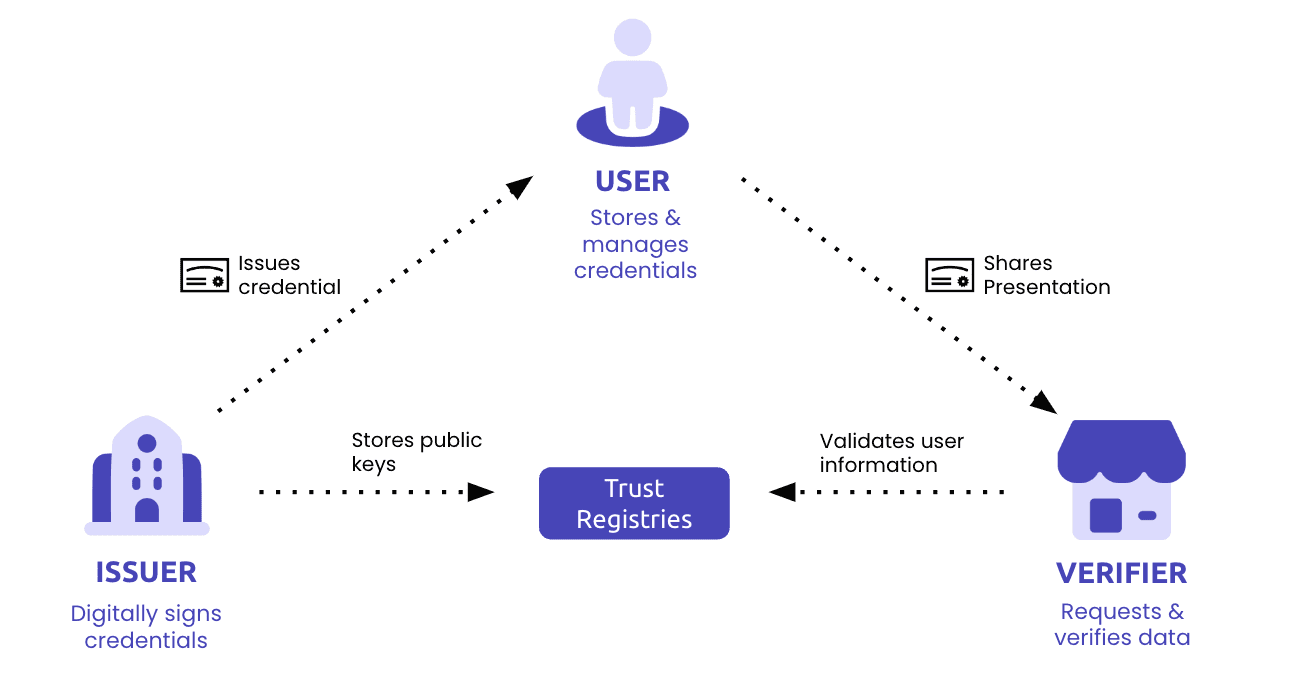
To help visualize the process, the diagram below illustrates the flow of a Verifiable Credential between the three main stakeholders in the SSI ecosystem: Issuers (who issue VCs), Holders (who store & share VCs), and Verifiers (who verify VCs). This is also known as the Trust Triangle.
Example - Applying for a Master's degree:
The user (holder) stores in their ID Wallet a national ID and an Academic Diploma in the form of Verifiable Credentials issued previously by the Government and the educational institution (Issuers).
The user sends the Master's University (verifier) a Verifiable Presentation containing the specific identity information required by the University for authentication (in this case, the National ID and the Diploma).
The University verifies the information instantly thanks to the already verified, cryptographically-signed Verifiable Credentials, which are automatically paired to a DID to prove the user is the subject of the information and the issuers are trusted authorities. This is achieved by leveraging blockchain or other Distributed Ledger Technologies (DLTs).
Once verified, the user gains access to their account on the University's online platform, all within a matter of seconds!
The issuance and verification processes can be easily configured in Gataca Studio, allowing you to meet regulatory standards. Get started with a 30-day free trial.
Benefits of Verifiable Credentials
So why should you care about VCs? Their benefits can vary depending on your particular context, but one thing is clear: their adoption creates a win-win scenario for both your organization and your clients.
Benefits for organizations
Verifiable Credentials unlock a world of simplicity for your organization. You can seamlessly and automatically verify user information without worrying over the legal validity of their credentials. This ensures only verified individuals can access your services while delivering a frictionless experience.
Imagine clients accessing your online services without the hassle of juggling multiple usernames and passwords. Users simply scan a QR code on your website, initiating the sharing of the required credentials, and voila – they're in. This not only reduces the steps needed for access but also significantly slashes onboarding abandonment rates.
Lastly, by eliminating the need to store extensive personal data and with compliance engrained, VCs reduce costs remarkably.
Benefits for individuals
Verifiable Credentials bring unparalleled convenience to end-users by simplifying the process of proving their identity and sharing information in online interactions. VCs eliminate the tiresome need to repeatedly provide the same information, transforming verification times from days to mere seconds.
Furthermore, VCs empower individuals with user control and data ownership. Users decide when, where, and with whom they share their information. This aligns perfectly with data protection regulations, given that VCs also allow users to selectively disclose only the necessary information for their verification.
Last but certainly not least, users can trust that their personal information remains impeccably secure. Verifiable Credentials are fortified with cryptographic security, offering robust protection against any potential breaches or tampering.
Components of a Verifiable Credential
Different elements of Verifiable Credentials (VCs) are crucial for defining how information is structured and securely exchanged. Let's break down these elements for a better understanding:
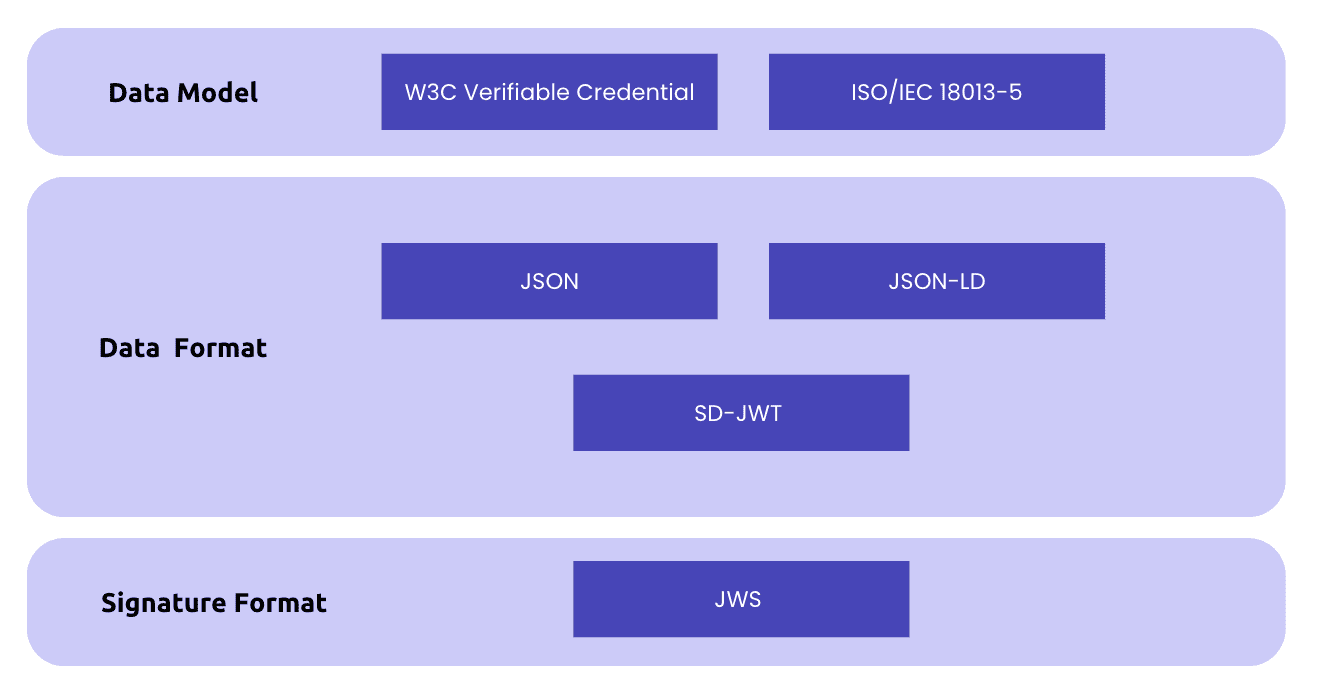
Data Model
Data models refer to standardized frameworks or schemas that define the structure and semantics of digital identity data.
ISO/IEC 18013-5 (mDL) and the World Wide Web Consortium (W3C) Verifiable Credentials Data Model (currently in version 2.0) have emerged as the two dominant standards for digital credentials. Yet, on the technical side, both standards are seemingly incompatible and the current debate revolves around finding how they can coexist and interoperate with each other.
On a high level, both the ISO mDL credential and VCs are composed of three main components:
- Credential Metadata: This contains crucial information about the credential itself, such as the credential type, issue date, and expiration date.
- Claims: These are statements or attributes about the subject of the credential, which could be an individual, a legal entity, or even a thing.
- Proofs: Here comes the cryptographic verification, in the form of a digital signature, ensuring that the credential genuinely originates from the claimed issuer and has remained untampered.
It is important to emphasize that no matter the attributes they contain, be it a national ID, an academic diploma, or a health record, all Verifiable Credentials follow the same structured format. This standardized approach offers the potential to exchange data between different actors, which simplifies logins across various services, even in regulated domains, and paves the way for a unified digital identity granting access to multiple online services.
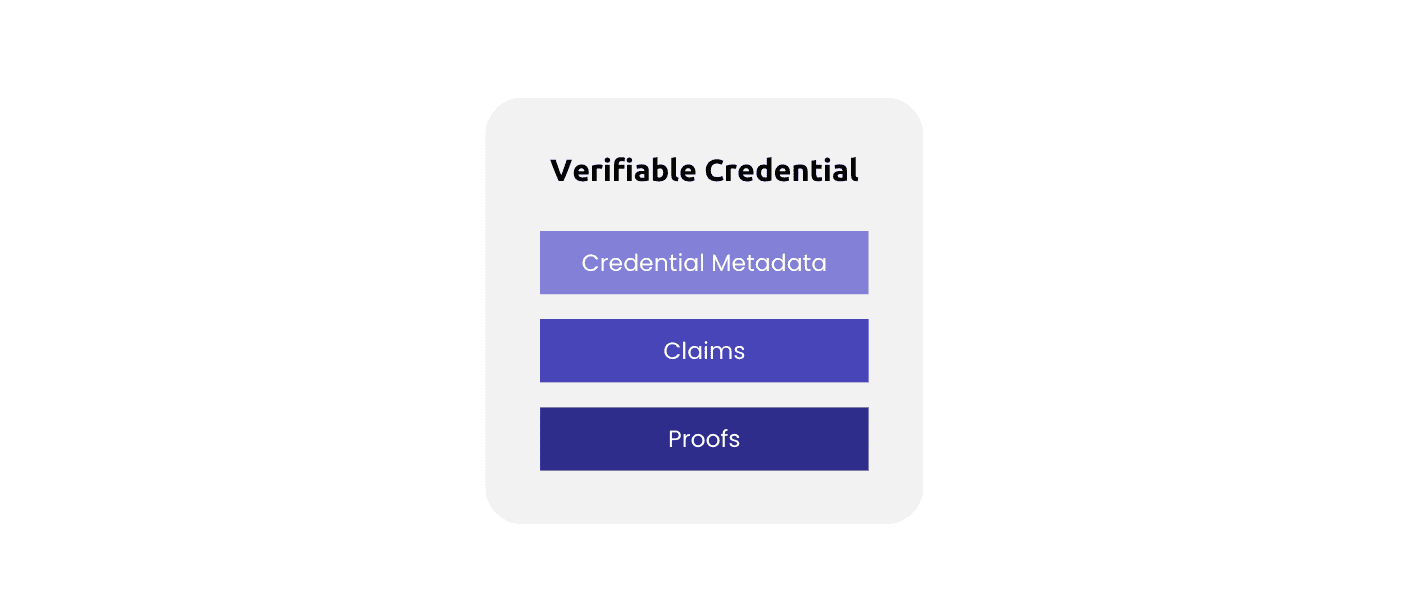
Let's see this structure using an example of an academic diploma VC:
The Metadata would include an identifier for this specific credential ("id12345678"), the DID of the issuer ("University of Madrid"), the type of credential ("Academic Diploma"), and the issuance date ("01/02/2023")
In the case of an academic diploma, the claims would encompass crucial information targeted at the student's DID. This information could include the type of degree, the graduation year, the grade achieved, and the number of credits completed.
The proofs would consist of cryptographic signatures from the issuing authority ("University of Madrid") to allow service providers to verify the authenticity and ownership of the credential.
Data Format
Data formats are specific representations of digital identity information based on a chosen data model governing how data is encoded, organized, and transmitted.
The VC data model defines two main data syntaxes: JSON and JSON-LD.
-
JSON is a text-based data format following JavaScript object syntax and is commonly used for transmitting data in web applications. This data format employs a straightforward key-value pair structure, making it easy for both humans and machines to read and write, but it lacks built-in mechanisms to specify data context.
-
JSON-LD is a lightweight Linked Data format. In contrast to JSON, it offers rich semantic context. JSON-LD allows the inclusion of information that clearly defines data properties and their meanings, making it the preferred choice for intricate and interconnected Verifiable Credentials.
However, a third data format that takes as an input a JSON or JSON-LD has quickly gained traction in Europe, with several implementations and adoption as an important building block in the latest EUDI Wallet Architecture and Reference Framework, is Selective Disclosure for JSON Web Tokens (SD-JWTs).
- SD-JWT is a mechanism for selective disclosure of particular components of a JSON object used as the payload of a JSON Web Signature (JWS) structure and enables users to share specific information or claims in a Verifiable Credential while keeping other information private (within bounds defined by the Issuer).
One of the challenges and ongoing discussions around SD-JWTs is their complexity of use for the end-user and limited ecosystem adoption compared to other standards. We have a detailed article on SD-JWT and other methods for implementing selective disclosure on Verifiable Credentials to dive deep into this topic.
Signature format
The signature format in a Verifiable Credential (VC) is a critical component that adds a layer of security and trust to the credential. Here, it is worth highlighting JWS (JSON Web Signature).
JWS secures content with digital signatures or Message Authentication Codes (MACs) using JSON-based data structures. It allows the attachment of a digital signature to the VC in a way that is both tamper-evident and verifiable.
A JWS consists of three main components: the header containing metadata about the signature, the payload with the VC data you want to sign, and the signature itself, generated by applying a cryptographic algorithm to the header and payload using a private key.
Verifiable Credentials Misconceptions
Understanding these misconceptions can help you make informed decisions when considering the adoption and implementation of Verifiable Credentials for your organization:
- Verifiable Credentials are the same as digital credentials: While Verifiable Credentials are a type of digital credential, they introduce unique qualities that go beyond what traditional digital credentials typically offer. The main distinction lies in the concepts of trust and verification. VCs incorporate cryptographic elements to ensure the integrity and authenticity of the credential. This cryptographic assurance allows anyone to independently verify the validity of the credential without relying solely on trust in the issuer.
- Verifiable Credentials are only for identity documents: While Verifiable Credentials can be associated with identity documents, it's essential to recognize their versatility. VCs can represent a wide range of claims and statements, making them applicable in various contexts beyond personal identity verification.
- Verifiable Credentials always require blockchain: Although blockchain technology is commonly mentioned in decentralized identity, it's not a mandatory component. Organizations can choose the most suitable technology stack based on their specific needs. For example, Gataca provides flexible integration capabilities with diverse blockchain networks, databases, and centralized Public Key Infrastructures (PKIs), among others.
- Verifiable Credentials are complex to implement: While the underlying cryptographic techniques can be complex, current decentralized identity solutions are becoming more accessible and user-friendly as the technology matures. Gataca Studio is a low-code platform that can be set up in seconds with our plug-and-play deployment system.
- Verifiable Credentials are only for online use: Verifiable Credentials can be used both online and offline. They can be stored in digital wallets and presented in various contexts, including face-to-face interactions, making them versatile for different scenarios.
UX/UI Design of VCs for Complex Data Models
User experience is the leading force behind the success and acceptance of any technology, and Self-Sovereign Identity is no exception.
At Gataca, we've put UX/UI design at the heart of our approach to Verifiable Credentials to ensure that your users can understand, interact with, and trust the information being presented. Let’s have a look at how.
- Simplified Complex Information: We use a visual hierarchy using labels, headings, and grouping to categorize related information, presenting the most important and relevant details first.
- Visual Data Relationships: Visual cues represent relationships between different components of Verifiable Credentials and can help users understand how different pieces of data are connected.
- Layered Information Presentation: Since VCs often have layers of information (issuer, subject, claims, etc.), we use different tabs and expandable sections. This prevents overwhelming users with too much information at once.
- Use Intuitive Icons: Incorporate intuitive icons and symbols to represent different types of data.

Our working group, UX4SSI, explores the intersection between User Experience and Self-Sovereign Identity to define best practices and reduce barriers to entry, promoting wider adoption of this technology.
Issue, Manage and Verify Verifiable Credentials with Gataca
Gataca Studio is a low-code decentralized identity verification platform designed for organizations that wish to implement Self-Sovereign Identity technology with little integration effort.
What can you do with Gataca Studio?
- Issue your own Verifiable Credentials: Create, validate, and digitally sign Verifiable Credentials. You can easily create credential issuance templates to integrate an issuance process into your website or application.
- Authenticate users in just one click: Gataca Studio enables you to quickly create customizable verification templates for onboarding and sign-in processes while reducing personal data stored in your infrastructure.
- Manage identity credentials in one place: Gataca Studio lets you effortlessly manage your company’s issued credentials, their status, and verified users from one dashboard.
For the end-user, Gataca Wallet is a mobile app providing users with unlimited, encrypted storage of verifiable credentials and allowing them to authenticate themselves seamlessly in digital services.
Ready to try it out? Get started with Gataca Studio or request a demo to discuss how Gataca can help with your authentication needs.

Esther Saurí
Digital Marketing Specialist